Table of Contents
What is A2SPA?
The A2SPA Verifier is a lightweight API service that validates inter-agent payloads in your environment with cryptographic precision. Unlike traditional security models that assume trust, A2SPA enforces it at the payload level.
Cryptographic Identity
Every payload is signed with RSA-SHA256 and verified against registered public keys
Zero-Trust Authorization
Granular permissions per agent with intent, scope, and target allowlists
Replay Protection
Built-in nonce and timestamp validation blocks duplicate requests
Full Audit Trail
Tamper-evident logging of every verification attempt and result
The 7 Layers of the AI Agent Stack
A2SPA operates as Layer 5 - the critical Trust Layer that every AI agent framework needs
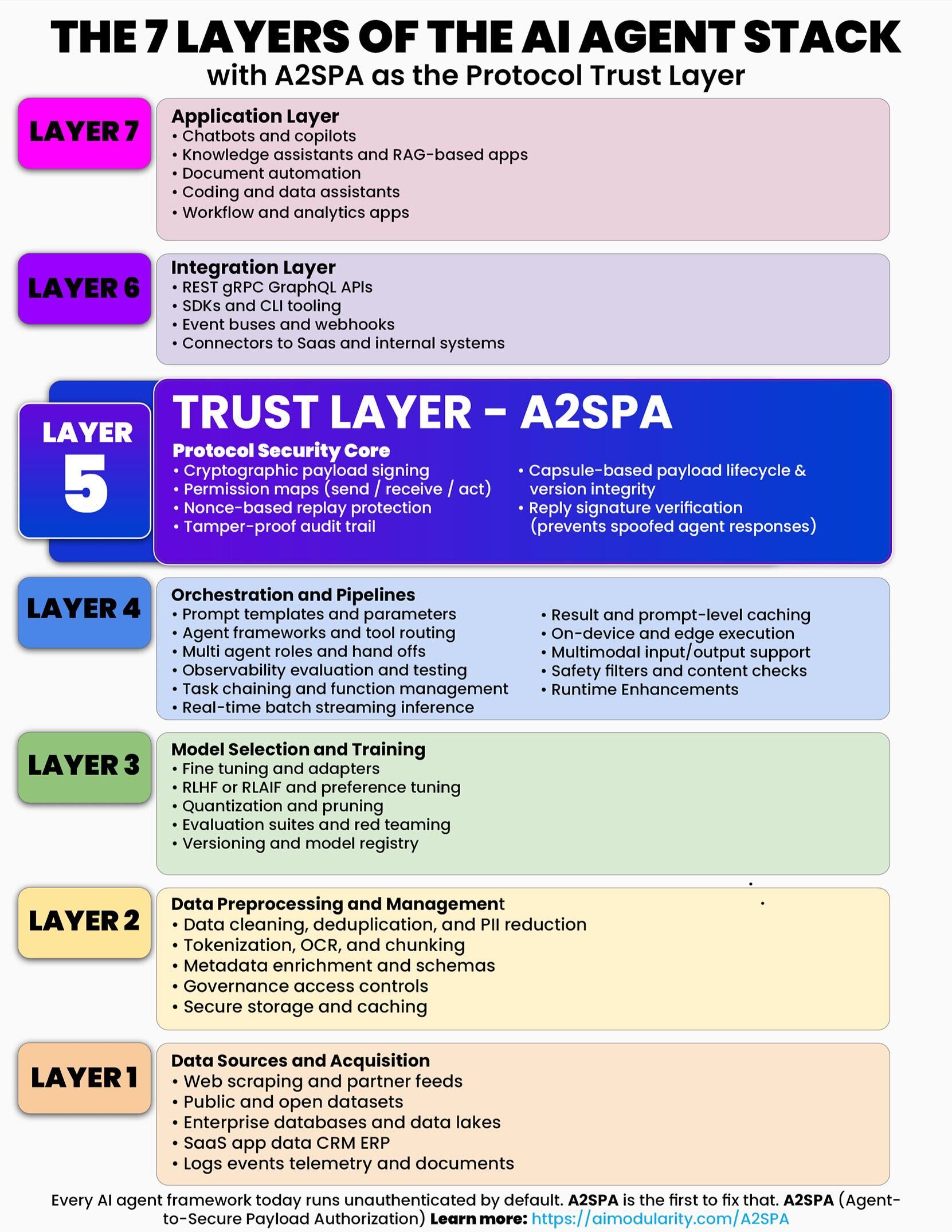
Every AI agent framework today runs unauthenticated by default. A2SPA is the first to fix that. A2SPA (Agent-to-Secure Payload Authorization) provides the missing cryptographic security layer that ensures every autonomous action is verified, authorized, and auditable.
Architecture Overview
▲ │
│ └─ Agent Registry + Audit Logs
│
License validation from /secrets/
Core Components
| Component | Purpose | Technology |
|---|---|---|
| A2SPA Verifier | FastAPI service that validates payloads | Python, Docker |
| PostgreSQL Database | Agent registry, nonce tracking, audit logs | PostgreSQL 15+ |
| License System | Offline validation of enterprise license | RSA signatures |
Core Security Features
Payload-Level Signature Enforcement
Every agent payload must be cryptographically signed with the sender's private key. The verifier validates signatures against registered public keys using RSA-SHA256 with PKCS#1 v1.5 padding.
# Payload signing process
1. Build canonical JSON (sorted keys, no spaces)
2. Compute SHA256 hash excluding the hash field
3. Sign the canonical bytes with agent's private key
4. Send: {"payload": {..., "hash": "..."}, "signature": "..."}
Zero-Trust Agent Authorization
Each agent is individually permissioned with modular access controls:
{
"send": true,
"receive": true,
"intents": ["ping", "email_outreach", "data_query"],
"scopes": ["test", "crm:write", "analytics:read"],
"allowed_targets": ["AGENT_RECEIVER", "AGENT_ANALYTICS"]
}
Replay Attack Immunity
Quick Start Installation
Prerequisites
- Docker 24+ and Docker Compose v2
- 1-2 CPU cores, 1-2 GB RAM
- Port 8081 accessible (or reverse proxy setup)
- Outbound internet for Docker image pulls
10-Minute Setup
# 1. Place license files
secrets/
license.json # your organization's signed license
public.pem # AImodularity licensing public key
# 2. Set database password
echo "POSTGRES_PASSWORD=your-secure-password" > compose/.env
# 3. Start the stack
cd compose
docker compose build
docker compose up -d
# 4. Verify health
curl http://localhost:8081/healthz
Agent Key Registration
# Generate agent keypairs
python examples/generate_rsa_keys.py --name AGENT_SENDER --out .
python examples/generate_rsa_keys.py --name AGENT_RECEIVER --out .
# Edit db/insert_agents.sql with your public keys
# Then apply the changes:
docker compose exec db psql -U a2spa -d a2spa -f /docker-entrypoint-initdb.d/02_insert_agents.sql
Enterprise Security Posture
Cryptographic Standards
- RSA-3072 keypairs minimum
- SHA256 hashing with canonical JSON
- PKCS#1 v1.5 signature padding
- AES-256 + TLS for transport
Deployment Security
- Air-gap friendly (offline licensing)
- VPC-native deployment
- mTLS and IP allowlisting support
- Minimal attack surface
Compliance Ready
- SOC2 audit trail support
- HIPAA compliant logging
- ISO 27001 evidence collection
- Tamper-evident log chains
API Reference
POST /verify_payload
Primary endpoint for payload verification
# Request Body
{
"payload": {
"version": 1,
"agent_id": "AGENT_SENDER",
"target_agent_id": "AGENT_RECEIVER",
"intent": "ping",
"scopes": ["test"],
"nonce": "abc123...",
"timestamp": "2025-08-25T15:00:00Z",
"hash": "sha256_hex_of_canonical_json"
},
"signature": "rsa_signature_hex"
}
# Success Response (HTTP 200)
{
"status": "VERIFIED",
"event_id": "evt_123...",
"agent_id": "AGENT_SENDER",
"target_agent_id": "AGENT_RECEIVER",
"timestamp": "2025-08-25T15:00:01Z"
}
# Failure Response (HTTP 400)
{
"detail": {
"error": "Signature verification failed",
"agent_id": "AGENT_SENDER",
"timestamp": "2025-08-25T15:00:01Z"
}
}
GET /healthz
Health check and license validation endpoint
# Response
{
"ok": true,
"license": {
"valid": true,
"expired": false,
"customer_id": "YOUR_ORG"
},
"database": {
"connected": true
}
}
Common Issues & Solutions
| Issue | Cause | Solution |
|---|---|---|
| Payload hash mismatch | Canonical JSON differs | Ensure sorted keys, no spaces, exclude hash field |
| Signature verification failed | Wrong key or encoding | Verify agent public key is registered correctly |
| Nonce replay detected | Reused nonce value | Generate fresh random nonce per request |
| Timestamp skew | System clock drift | Sync system time (NTP) or adjust A2SPA_MAX_SKEW |
| Policy denied | Insufficient permissions | Update agent permissions in insert_agents.sql |
Debug Commands
# View logs
docker compose logs verifier --tail=200
# Connect to database
docker compose exec db psql -U a2spa -d a2spa
# List registered agents
SELECT agent_id, enabled, permissions FROM agents;
# Check recent verifications
SELECT * FROM logs ORDER BY timestamp DESC LIMIT 10;
Common Issues & Solutions
| Issue | Cause | Solution |
|---|---|---|
| Payload hash mismatch | Canonical JSON differs | Ensure sorted keys, no spaces, exclude hash field |
| Signature verification failed | Wrong key or encoding | Verify agent public key is registered correctly |
| Nonce replay detected | Reused nonce value | Generate fresh random nonce per request |
| Timestamp skew | System clock drift | Sync system time (NTP) or adjust A2SPA_MAX_SKEW |
| Policy denied | Insufficient permissions | Update agent permissions in insert_agents.sql |
Debug Commands
# View logs
docker compose logs verifier --tail=200
# Connect to database
docker compose exec db psql -U a2spa -d a2spa
# List registered agents
SELECT agent_id, enabled, permissions FROM agents;
# Check recent verifications
SELECT * FROM logs ORDER BY timestamp DESC LIMIT 10;
Pricing
A2SPA secures agent-to-agent actions in your VPC. You get a compiled verifier container, a thin client SDK, and an offline license. Agents are not included (Bring-Your-Own-Agents).
Enterprise License (Annual)
What's Included
- Verifier container image (compiled; no app source)
- Thin client SDK (Python wheel) for hashing & signing
- Offline license (license.json + public.pem) — 1 year
- Postgres schema & templates
- Replay protection (nonce + timestamp)
- Zero-trust authorization
- Tamper-evident audit log (hash-chain)
- Quick-start & smoke test
- Email support: 24–48h first response
- Up to 8 hours remote onboarding
- Bug fixes & updates via new images
Price Levers (What Moves the Quote)
| Factor | Impact |
|---|---|
| Number of environments (stage/prod) and regions | Higher cost for multiple deployments |
| High-availability replicas | Additional licensing for HA setup |
| Hardening (mTLS, IP allow-listing, FIPS build) | Premium for enhanced security features |
| Immutable audit sink (WORM/S3 Object Lock) | Additional cost for tamper-proof retention |
| Onboarding hours beyond starter pack | Professional services hourly rates |
Bring-Your-Own-Agents (BYOA)
You connect your existing agents/services to A2SPA. We don't ship agent code by default.
Optional: Agent Enablement (Add-On)
For teams that want help wiring specific agents to A2SPA.
Policy design, keying, scopes/targets, test harness, rollout checklist.
Deployment Model
Private/VPC by Default
No outbound calls, air-gap friendly
Minimal Attack Surface
mTLS & IP allow-listing recommended
Your Data Stays Local
Data and logs remain in your environment
What You Receive After Purchase
📦 Container image tar (a2spa-verifier-<ver>.tar)
🐍 SDK wheel (a2spa_sdk-<ver>-py3-none-any.whl)
🔑 License files (license.json, public.pem) — 1-year term
🐳 Compose file, DB schema, agent insert template
✅ Smoke test script to verify end-to-end in minutes
FAQ
No. We're the security layer. You bring your agents; we can enable them as an add-on.
No. Licensing is offline; fully air-gapped is supported.
Base is tamper-evident (hash-chain). Add WORM/anchoring for tamper-proof retention.
Each unique agent_id that signs or verifies payloads (e.g., payments_writer, llm_router).
Next Step
Email hello@aiblockchainventures.com with:
- Company name
- Region(s)
- Environments (stage/prod)
- HA needs
- Number of agents you plan to secure
We'll reply with a one-page quote and an install checklist.