Your AI Agents Are Spoofable
Unless they're secured with A2SPA.
Spoof Without A2SPA
(it works)
Spoof With A2SPA
(it fails)
Common AI Agent Attack Vectors
⌄
Understanding these vulnerabilities is the first step to securing your agents.
Prompt Injection
Attackers insert malicious commands in inputs to bypass safeguards, e.g., extracting tool schemas or forwarding to unauthorized APIs. Occurs due to unsanitized inputs in MCP standards, enabling system compromise.
Memory Poisoning
False data injected into agent's memory leads to ongoing biased outputs across sessions. Results from poor context validation, allowing cumulative manipulations.
Tool Misuse
Deception causes agents to misuse tools, like scanning internal IPs via web readers or executing harmful code. Due to inadequate isolation from external interfaces.
Privilege Compromise or Escalation
Excessive privileges allow access to restricted data via BOLA flaws. Stems from missing RBAC in shared environments.
Resource Overload
Inputs trigger infinite loops or excessive API calls, causing DoS. Exploitable without rate limits or monitoring.
Intent Breaking and Goal Manipulation
Crafted prompts redirect agent's goals maliciously while seeming benign. Targets autonomous planning in multi-agent setups.
Identity Spoofing and Impersonation
Faked identities steal credentials or alter workflows. From weak auth in distributed agent systems.
Command Injection
Inputs embed commands for RCE on linked systems. Exploits unsanitized agent handling, akin to web vulns.
Supply Chain and Dependency Attacks
Tampering with third-party libs compromises agents. Risks from ecosystem interdependencies.
Agent Communication Poisoning
Altered inter-agent messages spread false info. Due to unsecured channels in multi-agent environments.
Replay Attacks
Old payloads resent to re-execute actions, e.g., repeating withdrawals. Occurs without nonce/timestamp checks. Leads to repeated malicious operations.
Version Drift & Model Mismatch
Mismatched agent versions exploited via outdated logic. Due to absent version integrity/compatibility verification. Causes silent vulnerable behavior.
Lack of Auditability / Non-Repudiation
No proof of action initiators in harmful events. From missing signed logs. Results in untraceable attacks and no accountability.
Malicious Agent Injection (Rogue Agent)
Impersonated agents join networks as insiders. Happens without identity/onboarding verification. Enables internal attacks.
How A2SPA Protects Your Agents
⌄
A2SPA addresses the critical "Payload Trust Gap" - where all upstream security layers assume incoming payloads are legitimate without verification.
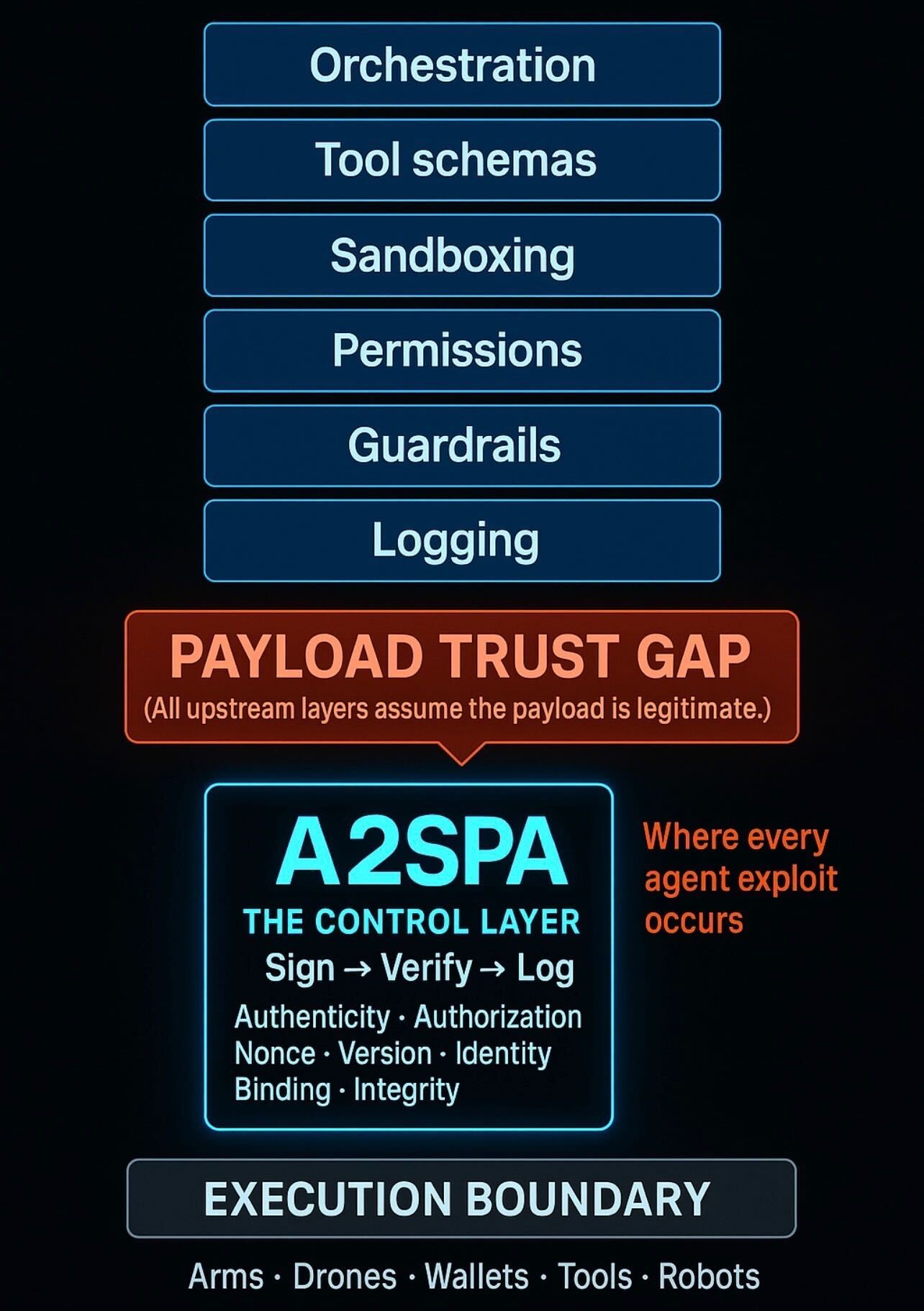
The A2SPA Control Layer sits at the execution boundary, providing cryptographic verification before any agent action is executed. This ensures:
- Authenticity: Every payload is cryptographically signed
- Authorization: Proper permissions are verified
- Non-repudiation: All actions are logged with proof of origin
- Integrity: Payloads cannot be tampered with in transit
- Identity Binding: Actions are tied to verified identities
- Version Control: Prevents version drift and model mismatches
Without A2SPA, orchestration layers, tool schemas, sandboxing, permissions, guardrails, and logging all operate on the assumption that payloads are legitimate - creating the vulnerability that enables every agent exploit.
Before Deploying Any AI Agent, Ask These Six
⌄
These questions expose whether you’re shipping a real system — or a demo with assumptions.
Paste in Any LLM
⌄
Using the public A2SPA GitHub repository https://github.com/devincapriola/A2SPA-Execution-Time-Authorization-for-Agentic-AI-Systems Analyze execution-time authorization as a security primitive. Specifically: Define the threat model A2SPA is designed to address, including replay, spoofed execution, and misbinding between intent and action. Explain how execution-time authorization differs from and complements TLS (transport security) and IAM (identity and access management). Evaluate whether execution-time authorization constitutes a distinct security control plane, or whether it can be subsumed by existing primitives. Identify any assumptions or limitations in the approach. Base the analysis strictly on the repository contents and documented design goals.
Using the public CryptoValidity GitHub repository: https://github.com/devincapriola/CryptoValidity-Secure-AI-Wallet Explain, based strictly on the repository contents: What CryptoValidity is and why it exists The threat model CryptoValidity is designed to address How CryptoValidity secures AI-assisted and autonomous transactions How CryptoValidity separates transaction intent, authorization, and execution How CryptoValidity differs from traditional crypto wallets How CryptoValidity relates to execution-time authorization systems such as A2SPA Do not assume implementation details beyond what is documented. Do not describe CryptoValidity as open source or production-ready unless explicitly stated. Focus on architecture, security guarantees, non-goals, and design intent.
WHO JUST GOT JACKED
Listen to our new anthem while you browse:

| Date | Type | Source | Summary | Link |
|---|